DevSecOps Best Practices: Securing the Software Development Lifecycle
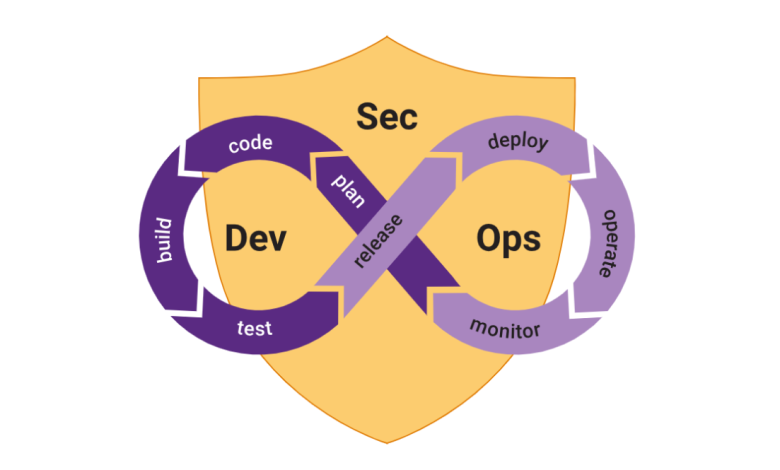
Introduction
In the rapidly evolving landscape of software development, security is a critical consideration that cannot be an afterthought. DevSecOps, a methodology that integrates security into the DevOps process, aims to bridge the gap between development, operations, and security teams. Explores the DevSecOps best practices, emphasizing the need for a proactive and collaborative approach to software security.
1. Understanding DevSecOps
DevSecOps is not just a set of tools but a cultural shift that emphasizes the importance of security from the beginning of the software development lifecycle (SDLC). Traditionally, security has been treated as a separate phase, often introduced late in the development process. DevSecOps challenges this paradigm, advocating for the integration of security practices at every stage of development.
2. Collaborative Culture
The success of DevSecOps hinges on fostering a collaborative culture among development, operations, and security teams. Communication channels should be open, and knowledge-sharing should be encouraged. Security experts should work alongside developers and operations personnel, breaking down silos and ensuring that security considerations are embedded throughout the development process.
3. Automated Security Testing
Automation is a cornerstone of DevSecOps. Automated security testing tools can scan code for vulnerabilities, ensuring that potential issues are identified and addressed early in the development process. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are crucial components of this automated testing approach, helping to catch security vulnerabilities in both the source code and the running application.
4. Continuous Monitoring
DevSecOps is not a one-time implementation; it’s an ongoing process. Continuous monitoring of the development environment, infrastructure, and application behavior is essential for identifying and responding to potential security threats. Automated monitoring tools can provide real-time insights into the security posture of applications and infrastructure, allowing for immediate action in the event of suspicious activities.
5. Infrastructure as Code (IaC) Security
With the rise of infrastructure as code (IaC), where infrastructure configurations are managed as code, securing the entire technology stack becomes imperative. DevSecOps practices involve incorporating security checks into IaC, ensuring that any changes to the infrastructure are compliant with security policies. This helps prevent misconfigurations and reduces the risk of security breaches stemming from vulnerabilities in the underlying infrastructure.
6. Container Security
Containers have become a standard in modern application development. DevSecOps extends its focus to container security, addressing vulnerabilities within container images and ensuring that runtime environments are secure. Continuous security scanning of container images, runtime monitoring, and implementing least privilege principles are essential aspects of container security in the DevSecOps paradigm.
7. Threat Modeling
DevSecOps emphasizes proactive security measures, and threat modeling is a key component of this approach. By identifying potential threats and vulnerabilities early in the development process, teams can prioritize and address security concerns before they become critical issues. Threat modeling encourages a proactive mindset, helping organizations stay one step ahead of potential security risks.
8. Secure Coding Practices
Developers play a pivotal role in the security of an application. DevSecOps promotes secure coding practices, encouraging developers to follow coding standards that minimize the risk of vulnerabilities. Training programs and regular code reviews can help ensure that developers are well-versed in secure coding principles and are equipped to write code that is resilient to security threats.
9. Continuous Integration and Continuous Deployment (CI/CD) Security
The speed at which modern development teams release software through CI/CD pipelines demands a security approach that keeps pace. DevSecOps integrates security into CI/CD processes, ensuring that security checks are part of the automated pipeline. This includes static code analysis, dependency scanning, and other security measures to validate that each code change meets security standards before deployment.
10. Incident Response Planning
Despite all preventive measures, security incidents may still occur. DevSecOps includes a robust incident response plan as a crucial component. Teams should be well-prepared to detect, respond, and recover from security incidents promptly. Regularly conducting incident response drills can help teams refine their processes and improve their ability to handle security incidents effectively.
11. Role-Based Access Control (RBAC)
Role-Based Access Control is a crucial aspect of DevSecOps that ensures the principle of least privilege is applied across teams. By assigning permissions based on job roles, organizations can limit access to sensitive information and functionalities, reducing the risk of insider threats. RBAC, when integrated into the DevSecOps pipeline, helps maintain a fine balance between collaboration and security.
12. Security Training and Awareness Programs
Human error remains one of the leading causes of security breaches. DevSecOps recognizes the importance of the human element and includes comprehensive security training and awareness programs. Ensuring that all team members are educated on the latest security threats, best practices, and the organization’s security policies creates a more vigilant and security-aware workforce.
13. Third-Party Component Security
Modern applications often rely on third-party components, libraries, and APIs. DevSecOps practices involve continuous monitoring and assessment of these components for known vulnerabilities. Dependency scanning tools can automatically detect and alert teams about outdated or compromised third-party components, enabling prompt updates or replacements to maintain a secure codebase.
14. Data Encryption Throughout the Pipeline
Protecting sensitive data is a top priority in DevSecOps. Implementing end-to-end encryption ensures that data remains secure both in transit and at rest. This includes encrypting data during transmission between different components of the application and securing data storage to prevent unauthorized access. By making encryption an integral part of the development pipeline, organizations fortify their defenses against data breaches.
15. Cloud Security Best Practices
As organizations increasingly migrate to cloud environments, DevSecOps extends its focus to cloud security. This involves implementing cloud security best practices, including proper configuration of cloud services, continuous monitoring of cloud infrastructure, and ensuring that data stored in the cloud is adequately protected. Cloud-native security tools are integrated into the DevSecOps toolchain to enhance the security posture of cloud-based applications.
Conclusion
DevSecOps is not just a set of practices; it’s a mindset that places security at the core of the development process. By integrating security from the outset, organizations can create a more resilient software development lifecycle, reducing the risk of security breaches and minimizing the impact of potential incidents. Embracing DevSecOps best practices is not only a response to the evolving threat landscape but a strategic move toward building a more secure future for software development.





